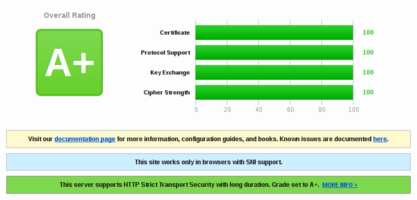
100/100/100/100% with A+ is possible on SSLLabs. But not useable... Because most Browsers do not support these ciphers...
You just have to remove all 128 Bit AES Ciphers (and some others):
$ openssl ciphers -v | egrep -v "MD5|RC4|LOW|3DES|PSK|SRP|DSS|EXP|SEED|aNULL|eNULL|SHA1|128" | grep -v "Kx=RSA" | cut -d " " -f 1 | xargs | tr " " ":"
ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:DH-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DH-RSA-AES256-SHA256:ECDH-RSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES256-SHA384
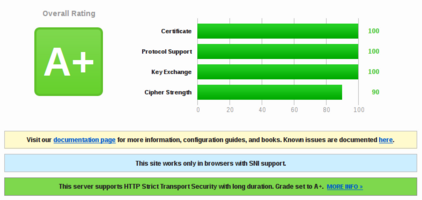
The best i can get (which is useable) is A+ but only 90% on Cipher Strength. Thats because you have to allow some AES128 Ciphers to work with Firefox and others.
Here are the Chipers:
$ openssl ciphers -v | egrep -v "MD5|RC4|LOW|3DES|PSK|SRP|DSS|EXP|SEED|aNULL|eNULL|SHA1" | grep -v "Kx=RSA" | cut -d " " -f 1 | xargs | tr " " ":"
ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:DH-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DH-RSA-AES256-SHA256:ECDH-RSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES256-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:DH-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DH-RSA-AES128-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-GCM-SHA256:ECDH-RSA-AES128-SHA256:ECDH-ECDSA-AES128-SHA256